A Step-by-Step Guide to Creating an IAM User
Hey there, cloud enthusiasts. Buckle up, because today we’re diving into the world of AWS Identity and Access Management (IAM). Now, we all know security is of great importance. But let’s be honest, sometimes convenience can cloud our judgment. Using the root user for everything might seem like a straightforward easy option, but it’s a security nightmare waiting to happen. Imagine handing your master key to everyone – that’s essentially what you’re doing with the root account. One compromise, and your entire AWS infrastructure is at risk.
Here’s where IAM users come in. Think of them as individual accounts with specific permissions. Need someone to manage S3 buckets? Create an IAM user with S3 access. Got a developer who only needs to deploy code? Create an IAM user for that too, with limited privileges.
THE ADVANTAGES OF IAM USERS
Granular Control: Assign permissions with laser focus. No more giving certain individuals more access than they need, everyone is granted access based on the rule of least privilege.
Security Best Practice: It’s an industry standard for a reason. Creating IAM users shows that you take a proactive approach to securing your AWS infrastructure.
Minimized Damage Potential: If one IAM user gets compromised, the damage is contained. Other IAM users and your core AWS environment remain protected.
Improved Audit Trails: IAM user activity logs provide a detailed record of actions performed within your account, allowing you to track exactly who did what within your account.
Creating IAM users is simple. With just a few clicks in the IAM console, you can easily secure your AWS resources. Additionally, there are numerous pre-built policies available to help you get started, eliminating the need to create permissions from scratch.
This guide details creating an IAM user with programmatic access. These credentials, Access Key and Secret Access Key, allow developers and DevOps engineers to securely interact with AWS programmatically using the AWS CLI, SDKs, or development tools. This eliminates the need for manual console login and empowers automation of tasks, resource management, and programmatic interactions with AWS services.
CREATING AN IAM USER ON AWS
Step 1: Create a New AWS user
1. Log in to the AWS Management Console using your root account credentials.
2. Navigate to the IAM service by searching for IAM① and click the IAM② service.
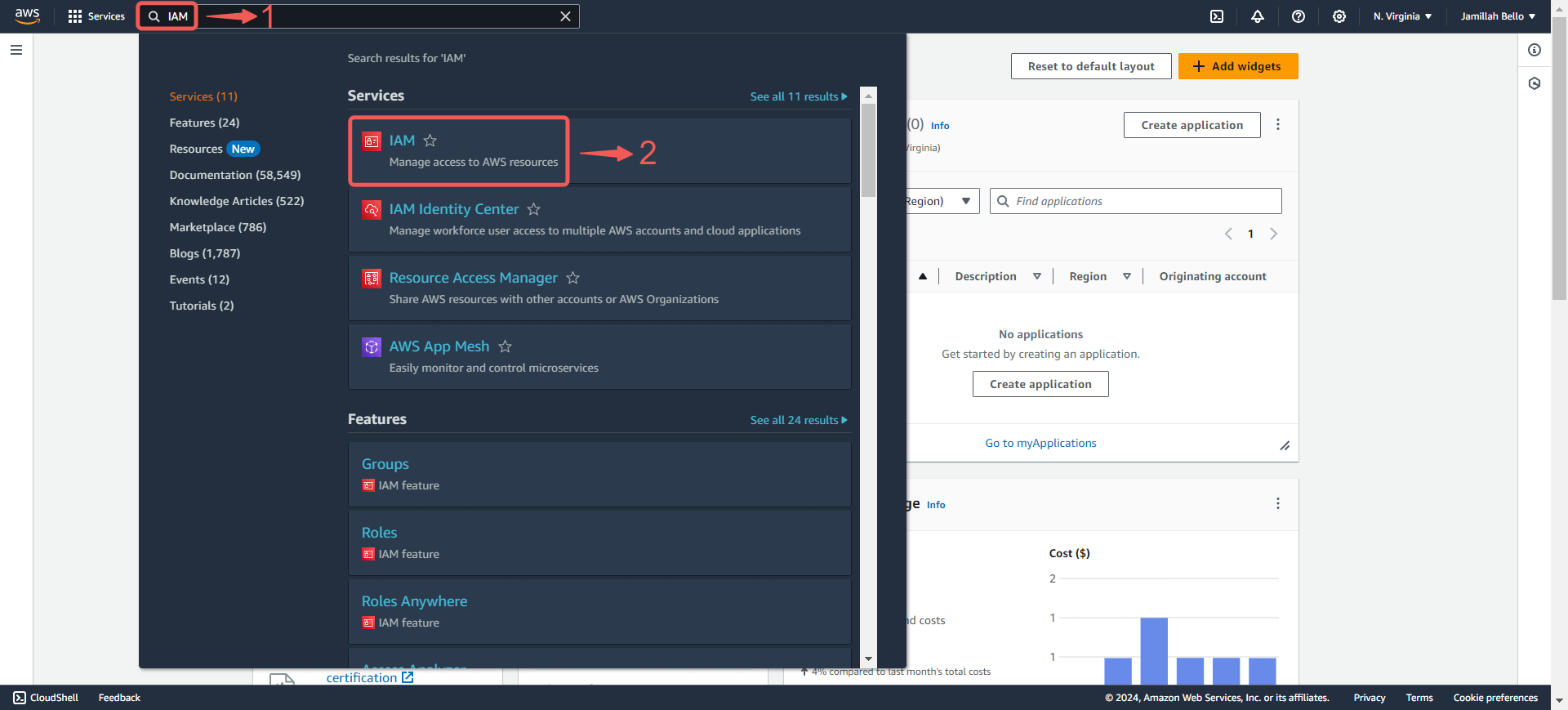
3. Click on the Users③ tab in the left navigation menu, and then click the Create user④ button.
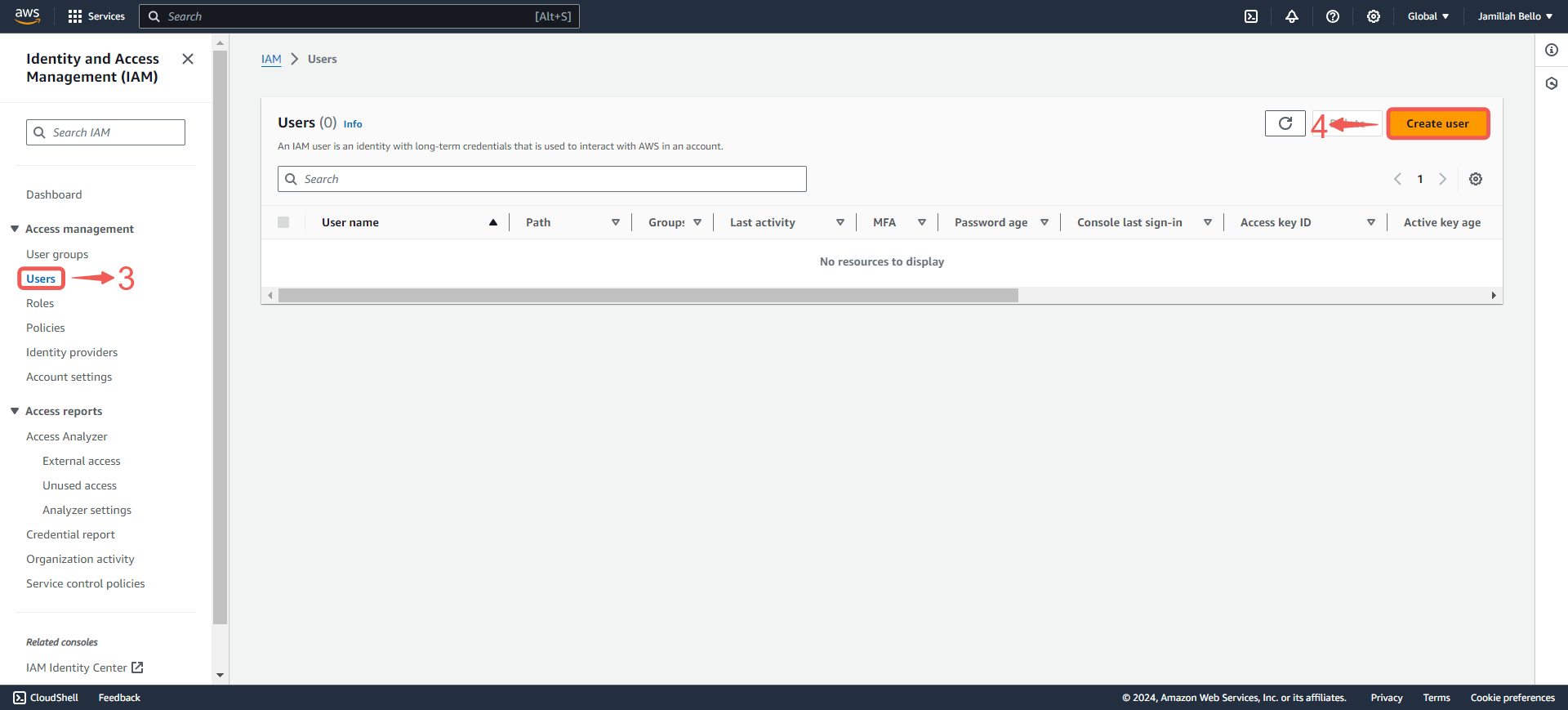
4. Write your User name⑤ and click Next⑥.
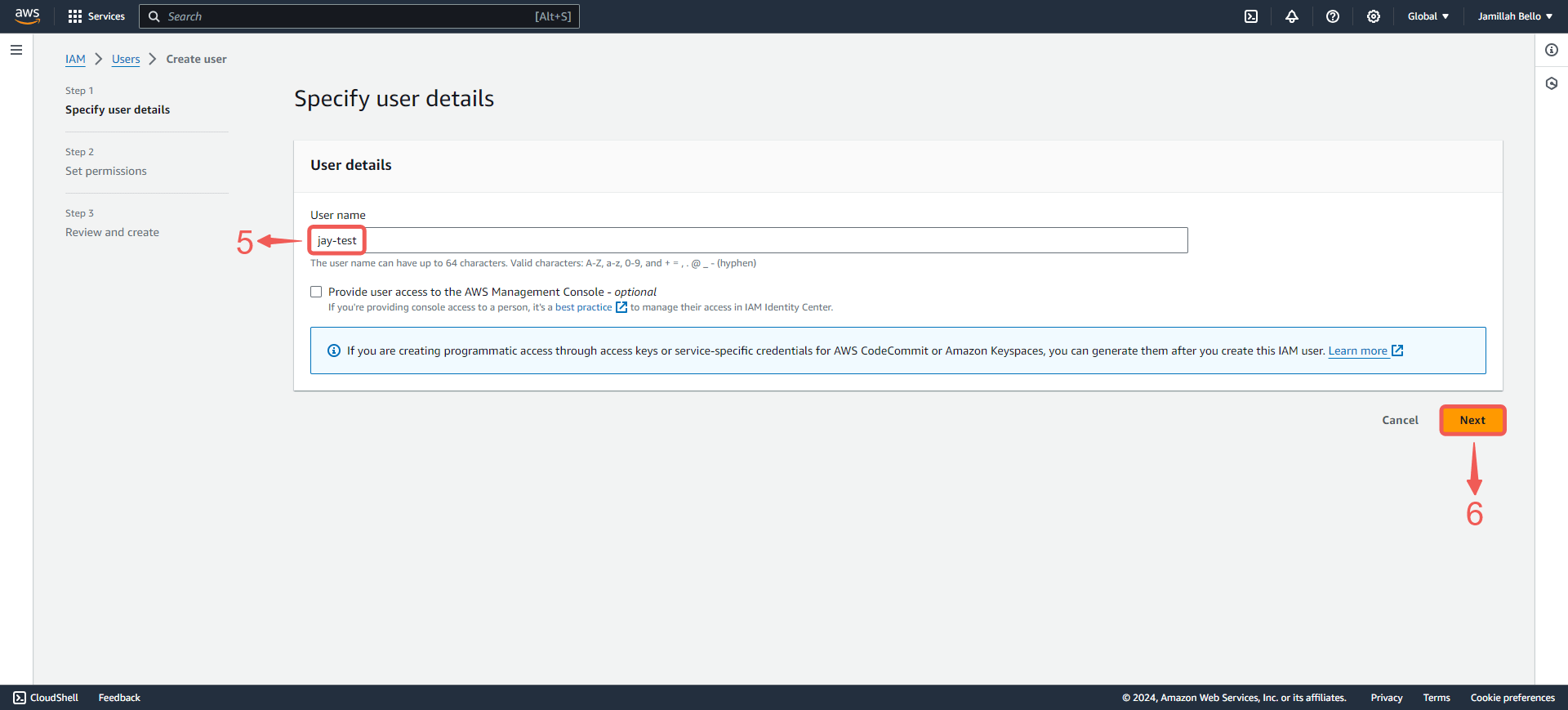
Note: This user account is being created for programmatic access only. Therefore, the console access checkbox will be left unselected.
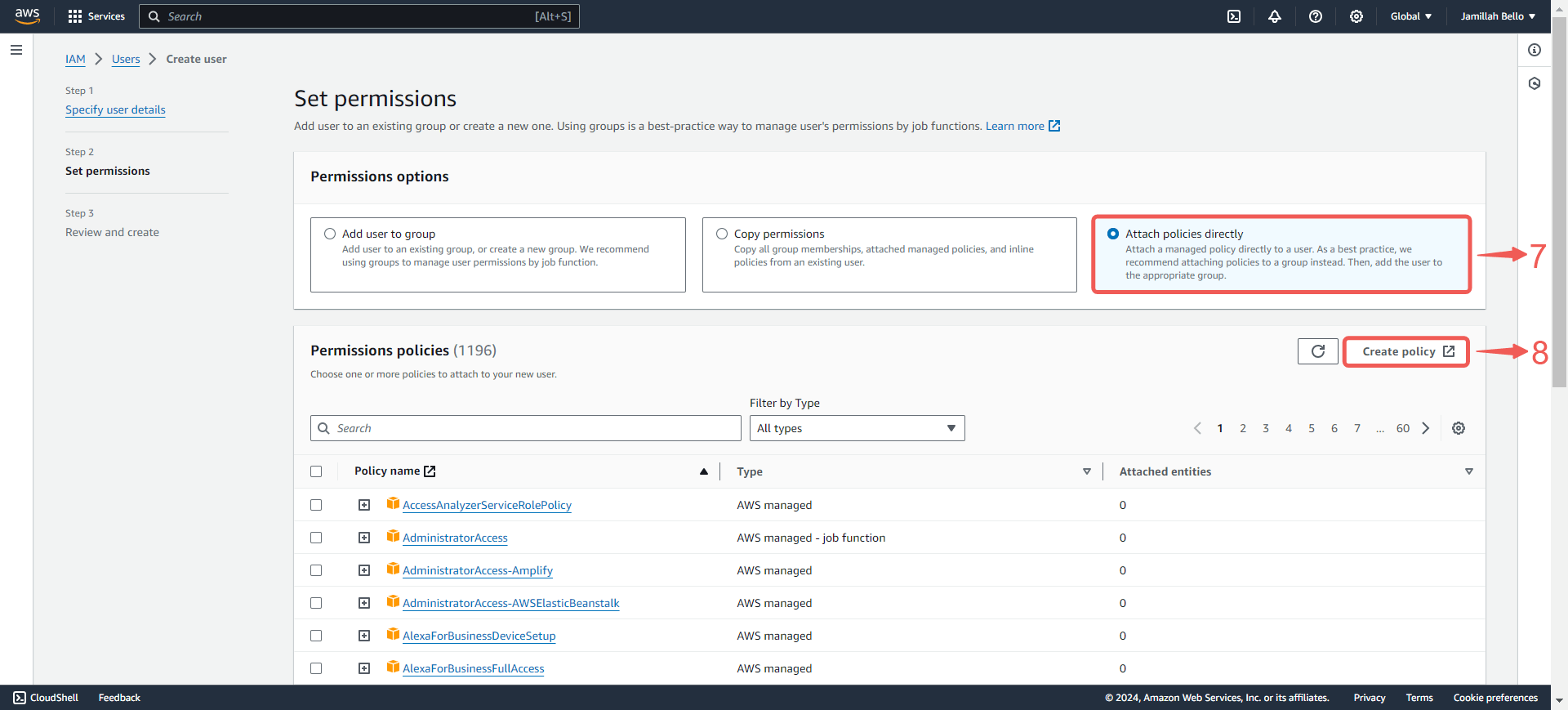
5. Select Attach policies directly⑦, and click on Create policy⑧.
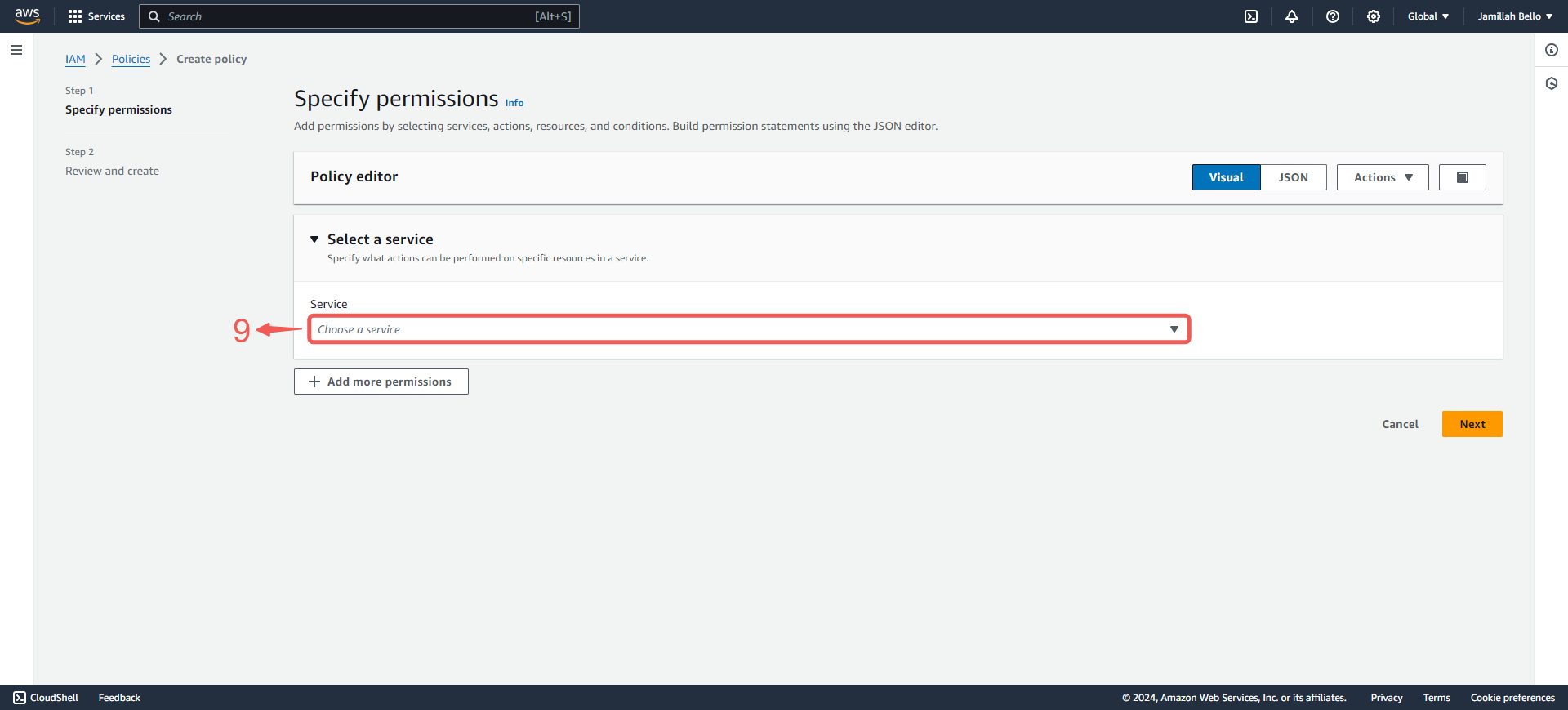
6. Click on Choose a service⑨ to open the dropdown menu.
7. Select Cost Explorer Service⑩.
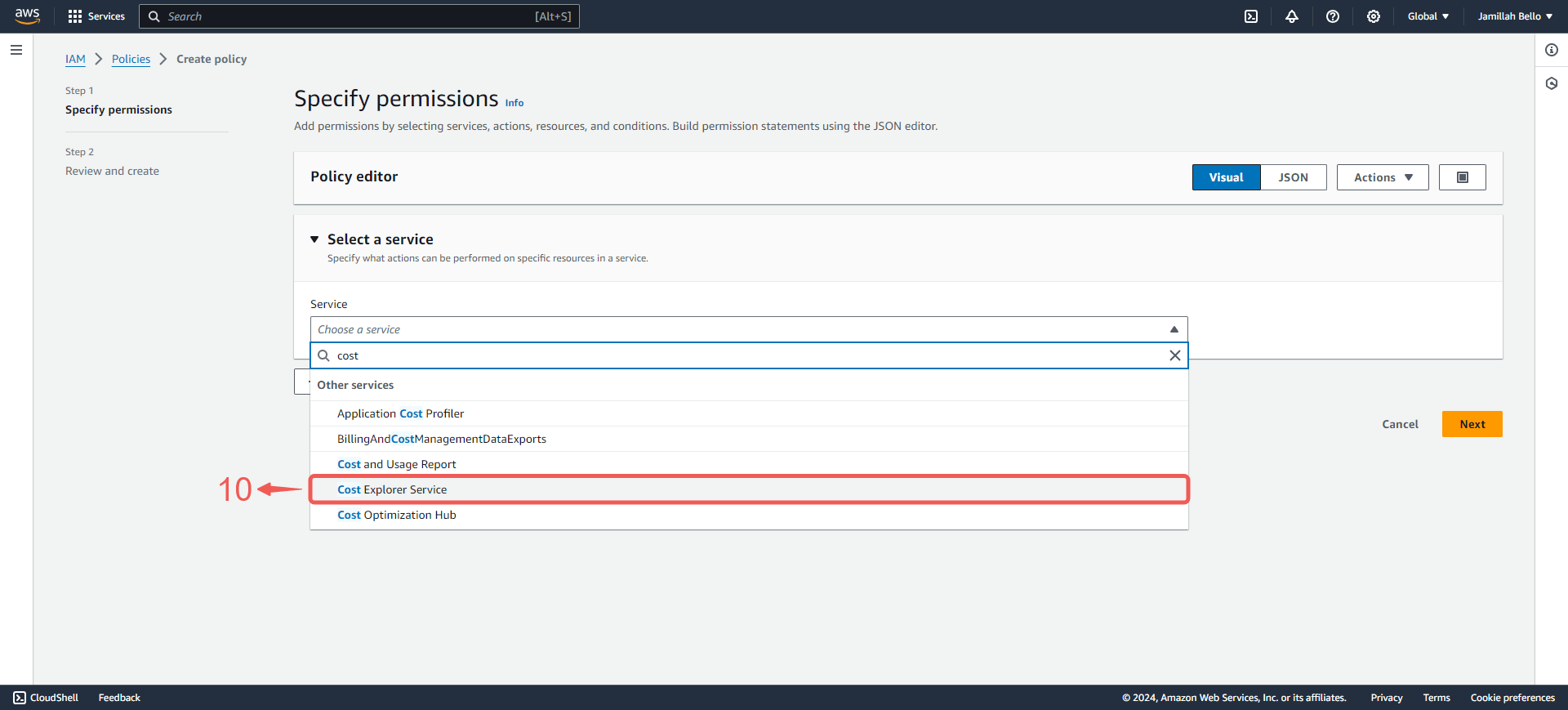
Note: Permissions depend on access needs. In this case, I’m choosing Cost Explorer to grant this user permission to access billing information for this AWS account.
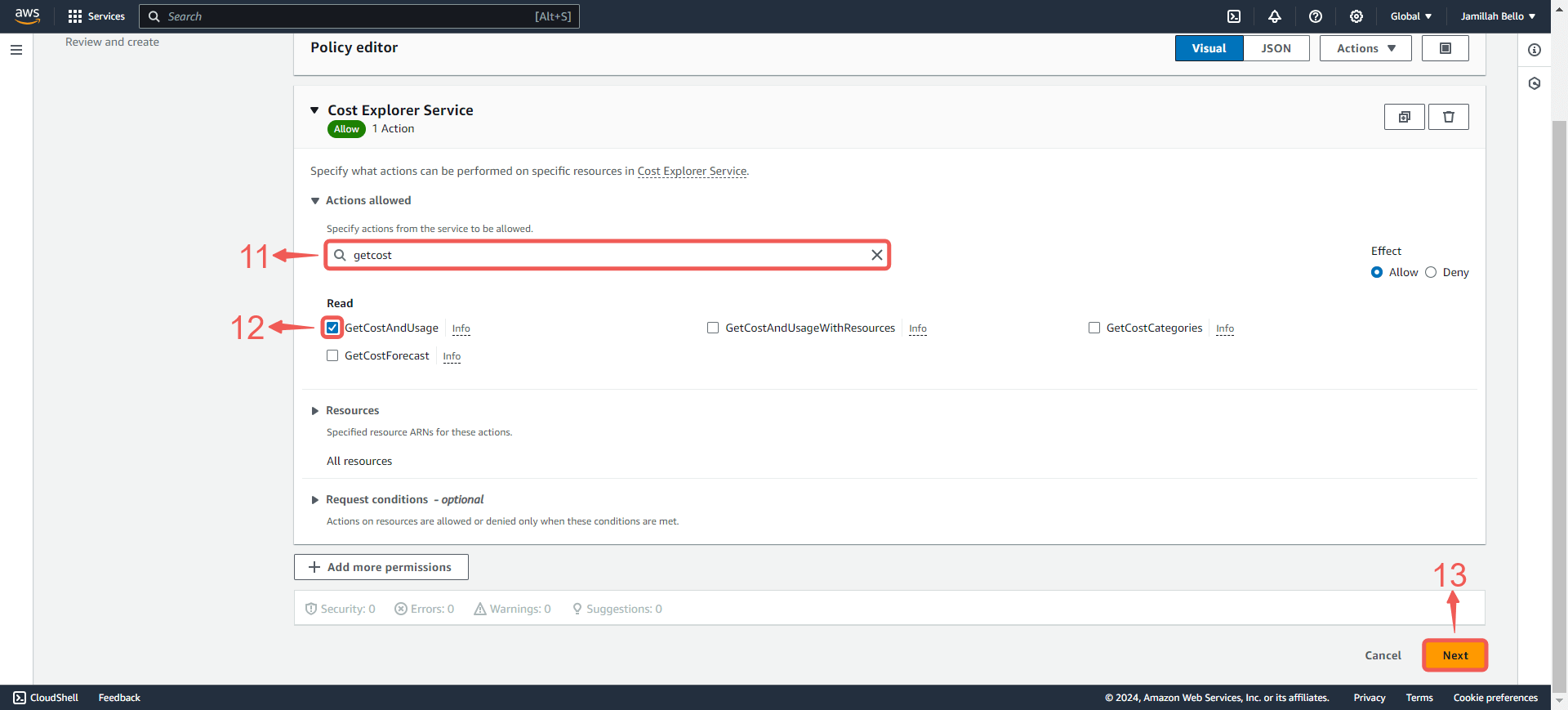
8. Search for the following policy:
GetCostAndUsage⑪, tick the box⑫ to select it, and then press Next⑬ to proceed to the next page.
9. Name⑭ your policy.
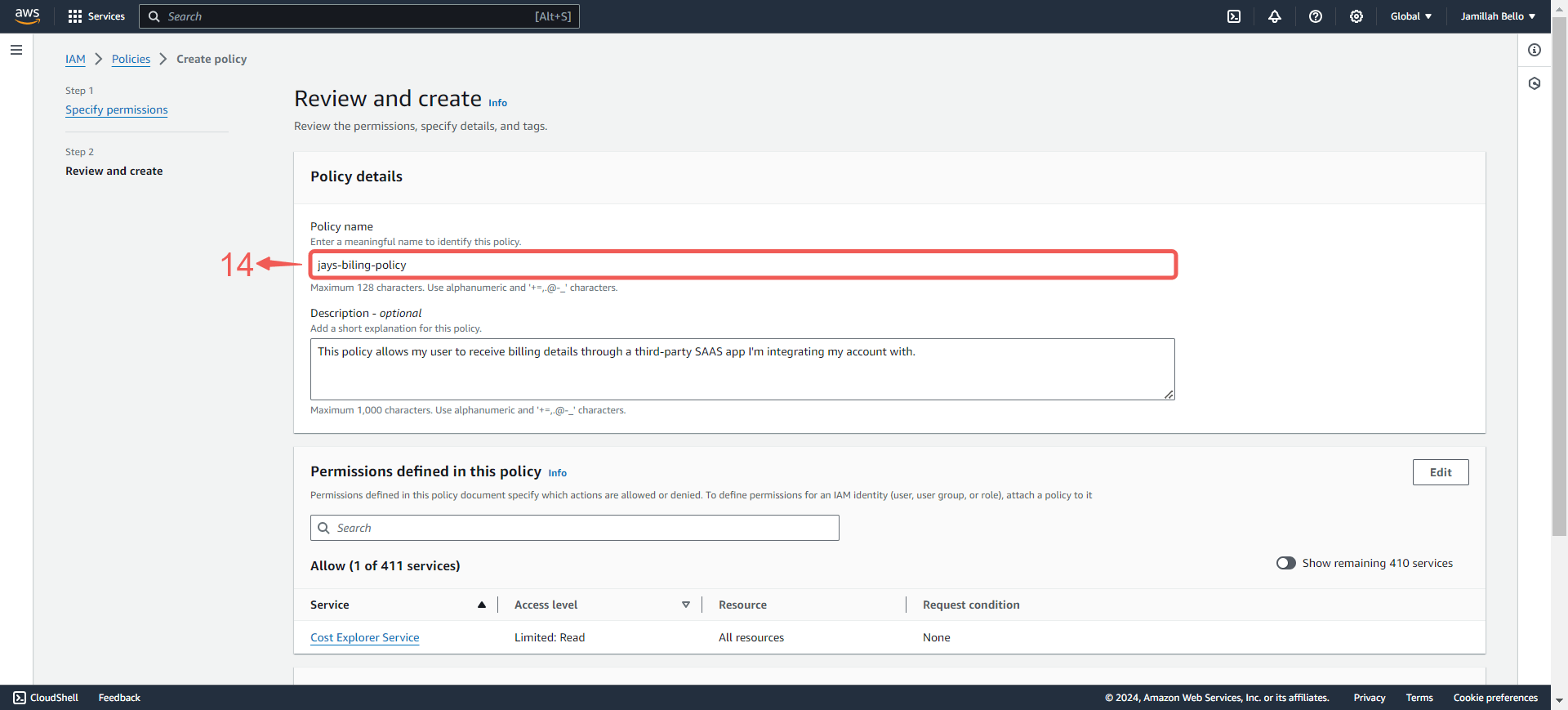
10. Click Create policy⑮.
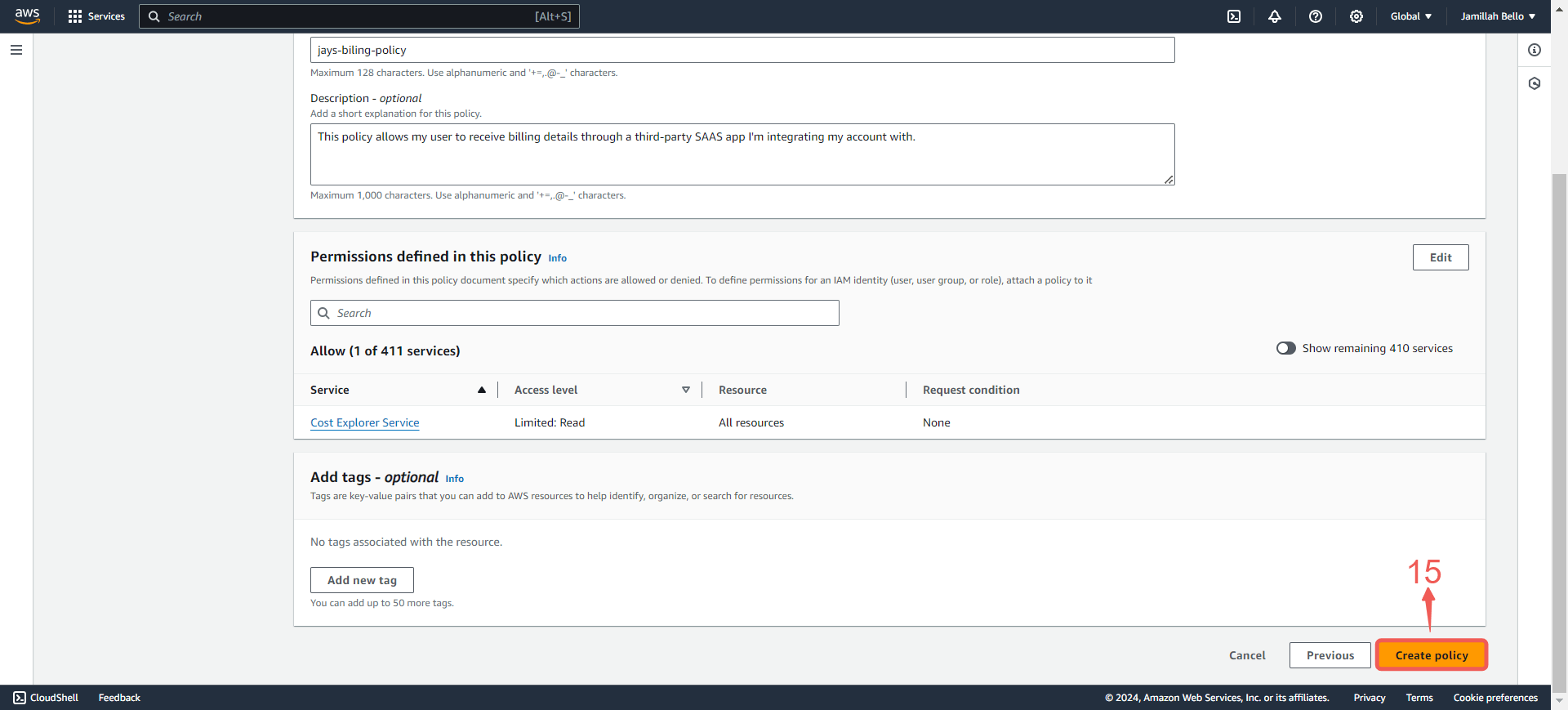
11. Return back to your previous `TAB`⑯.
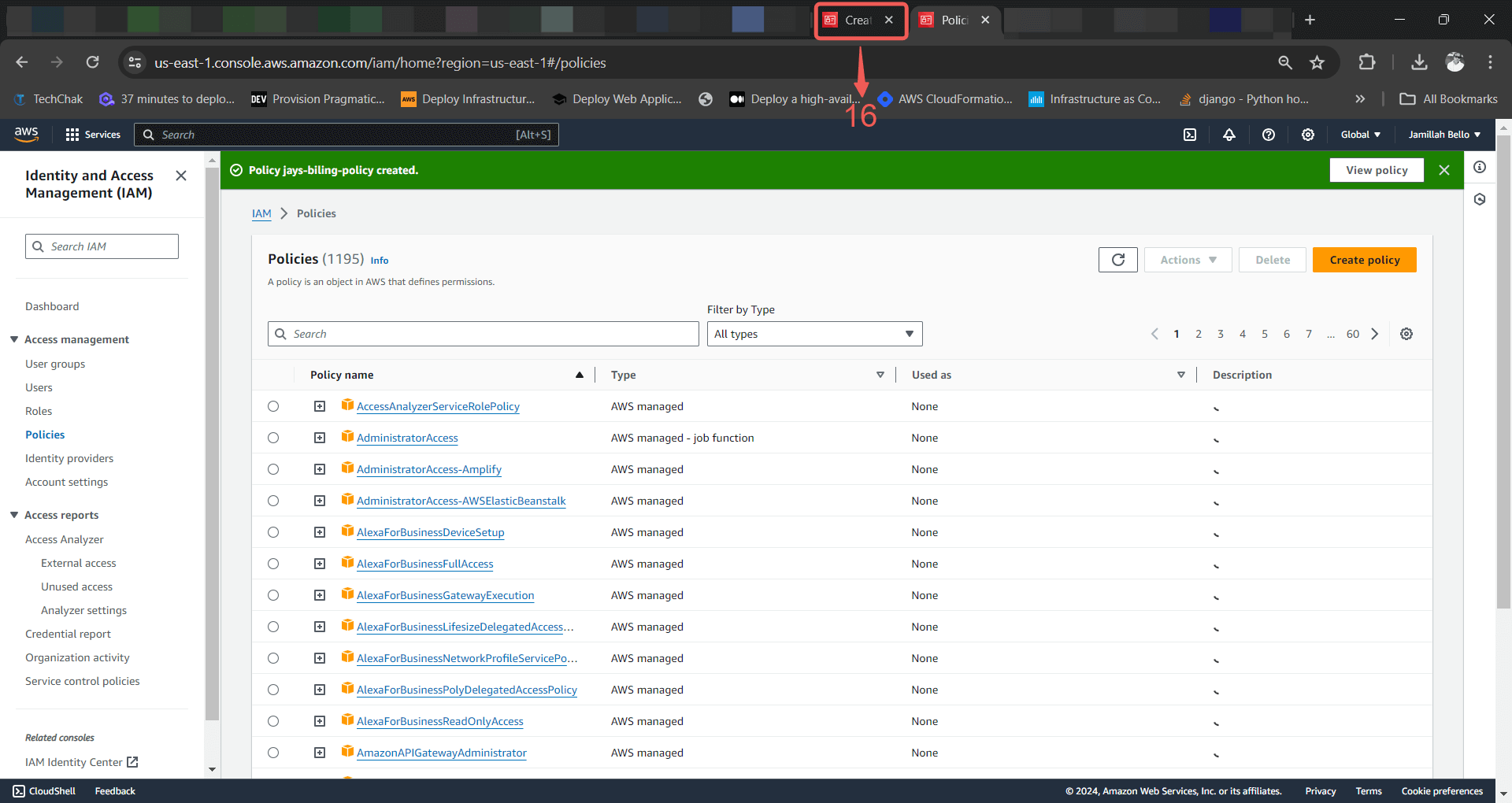
12. Refresh⑰ the policy list, search⑱ for your custom policy, check the box⑲ next to it to add it to your account, and then click on Next⑳.
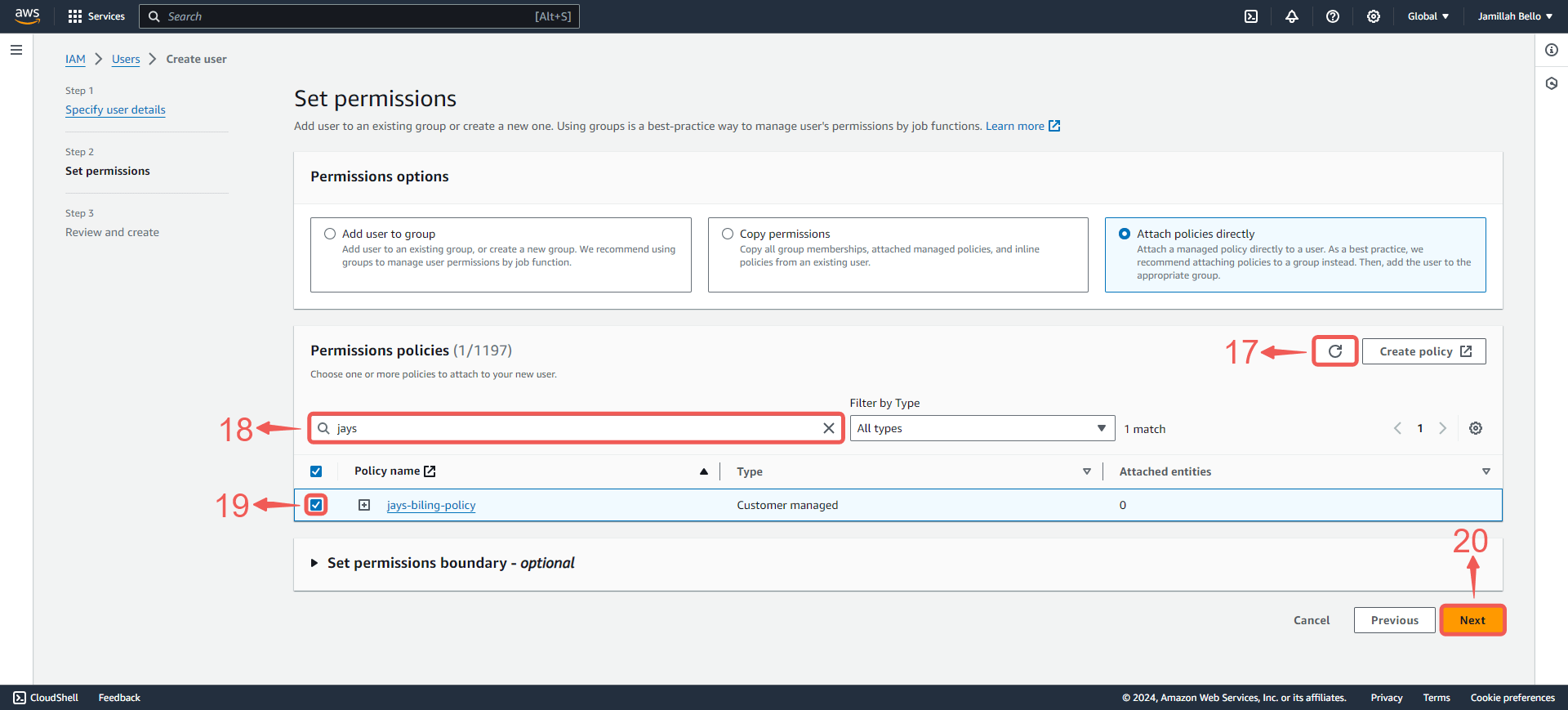
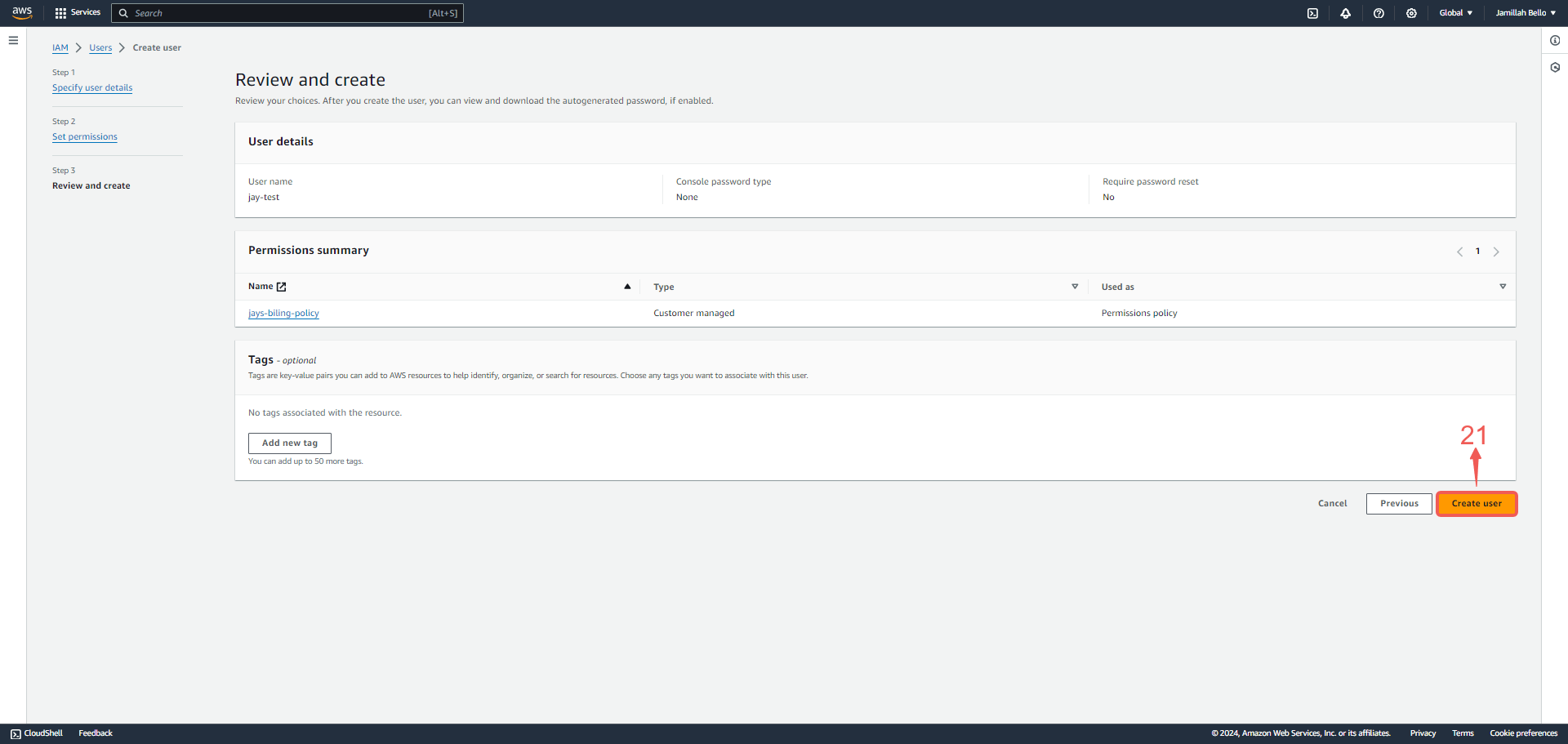
13. Review and press Create user㉑.
Step 2: Create an Access Key and Secret Access Key
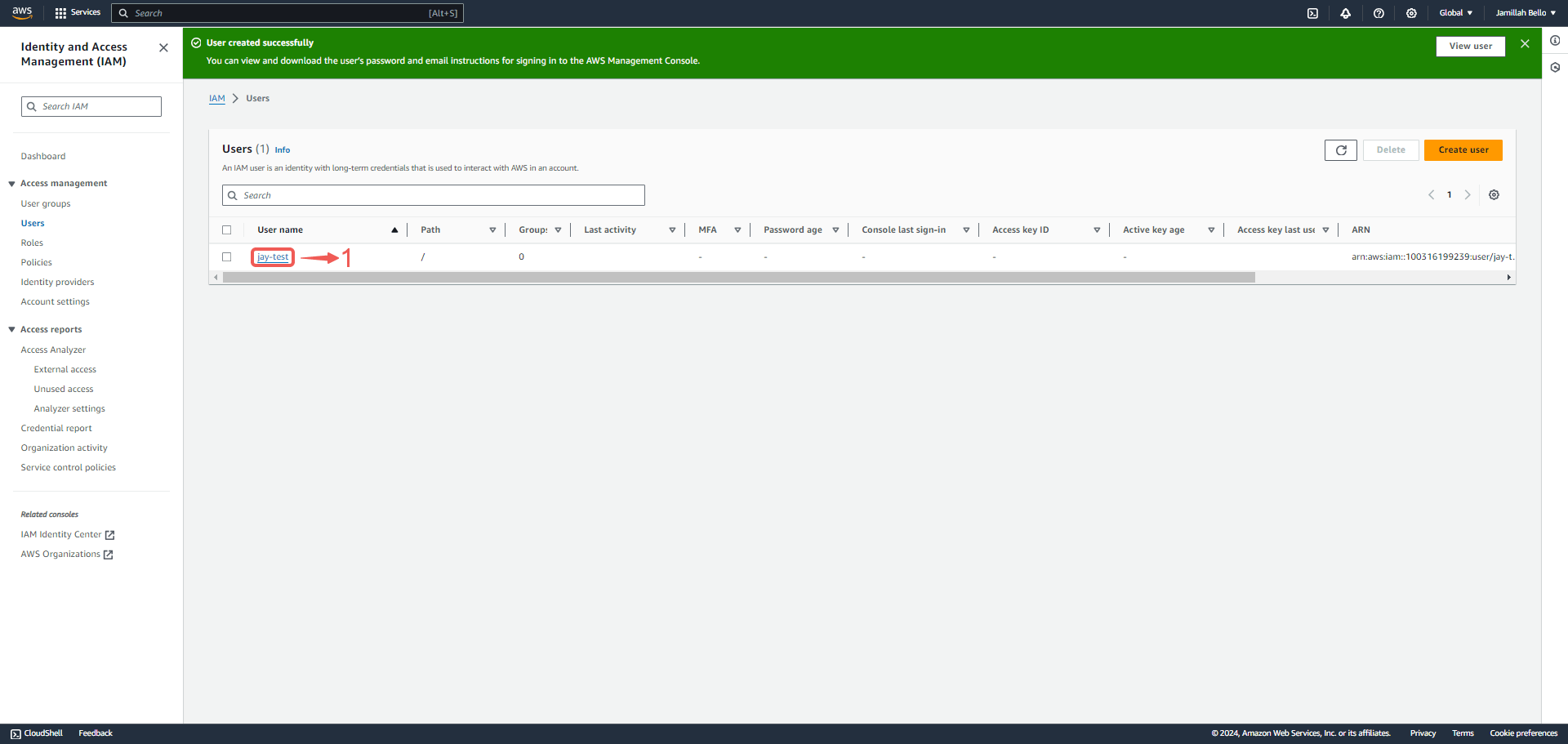
1. Now click on the user① you just created.
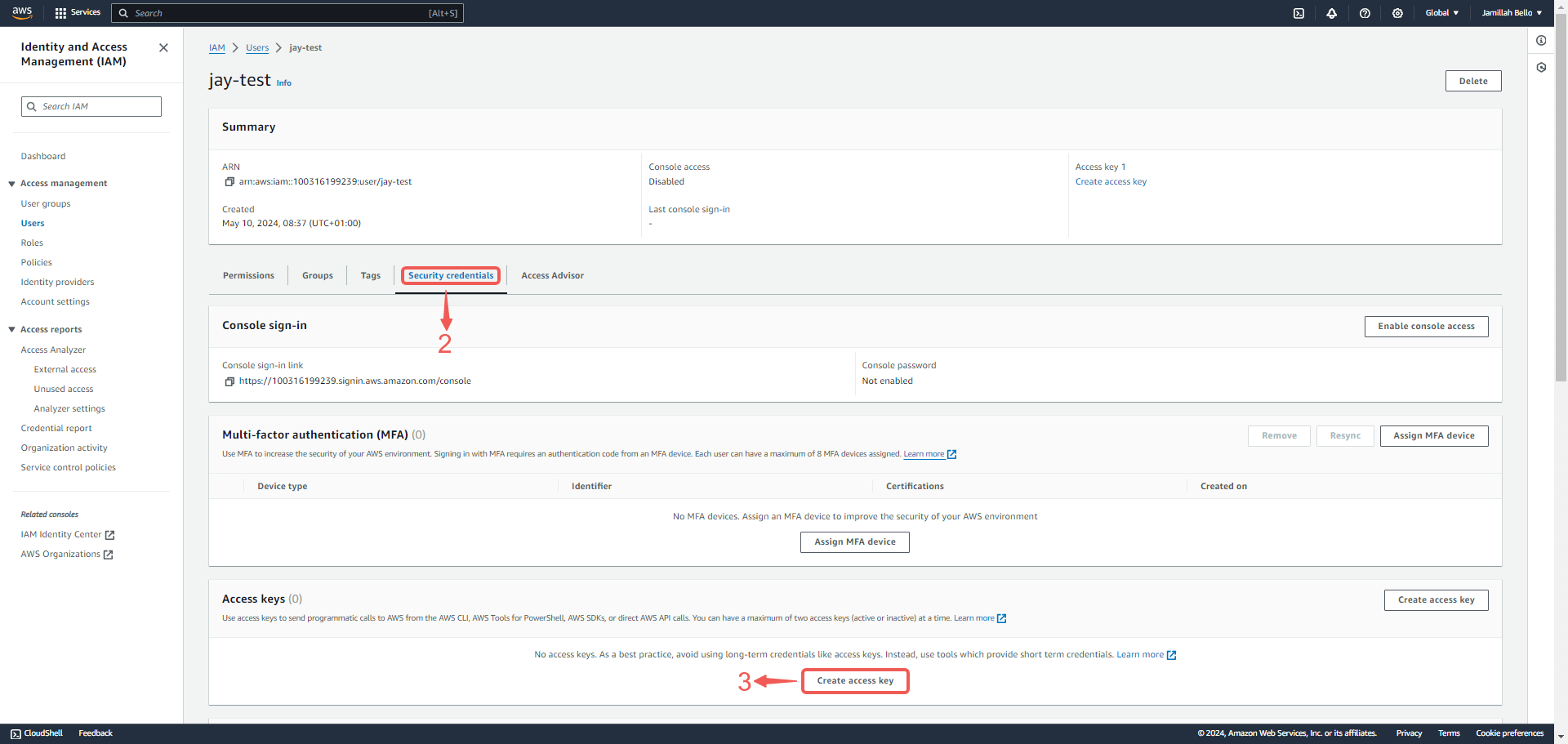
2. Under Security credentials② scroll down the page to `Access Keys`, and Click Create access key③.
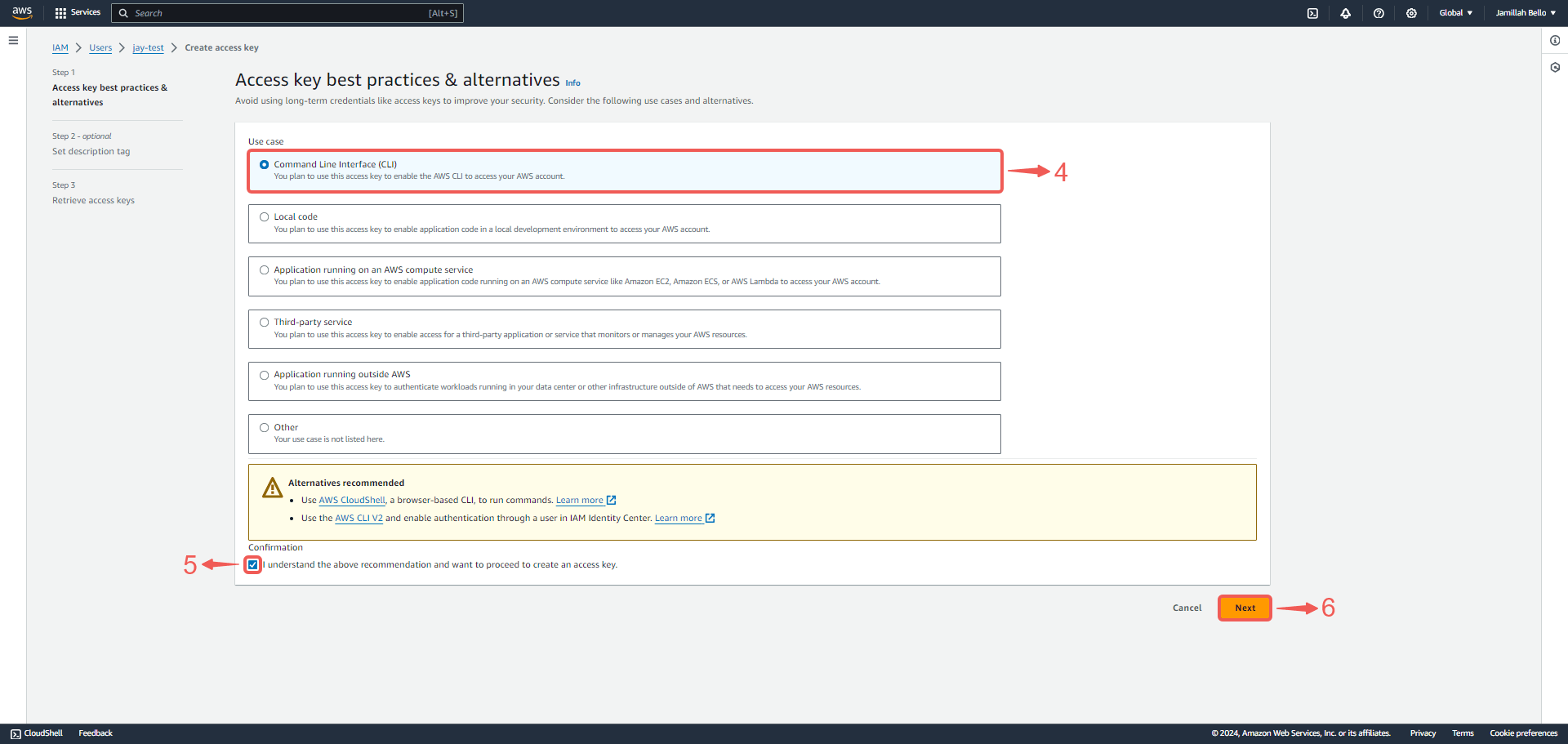
3. Select Command Line Interface (CLI)④, tick the Confirmation box⑤ and click Next⑥.
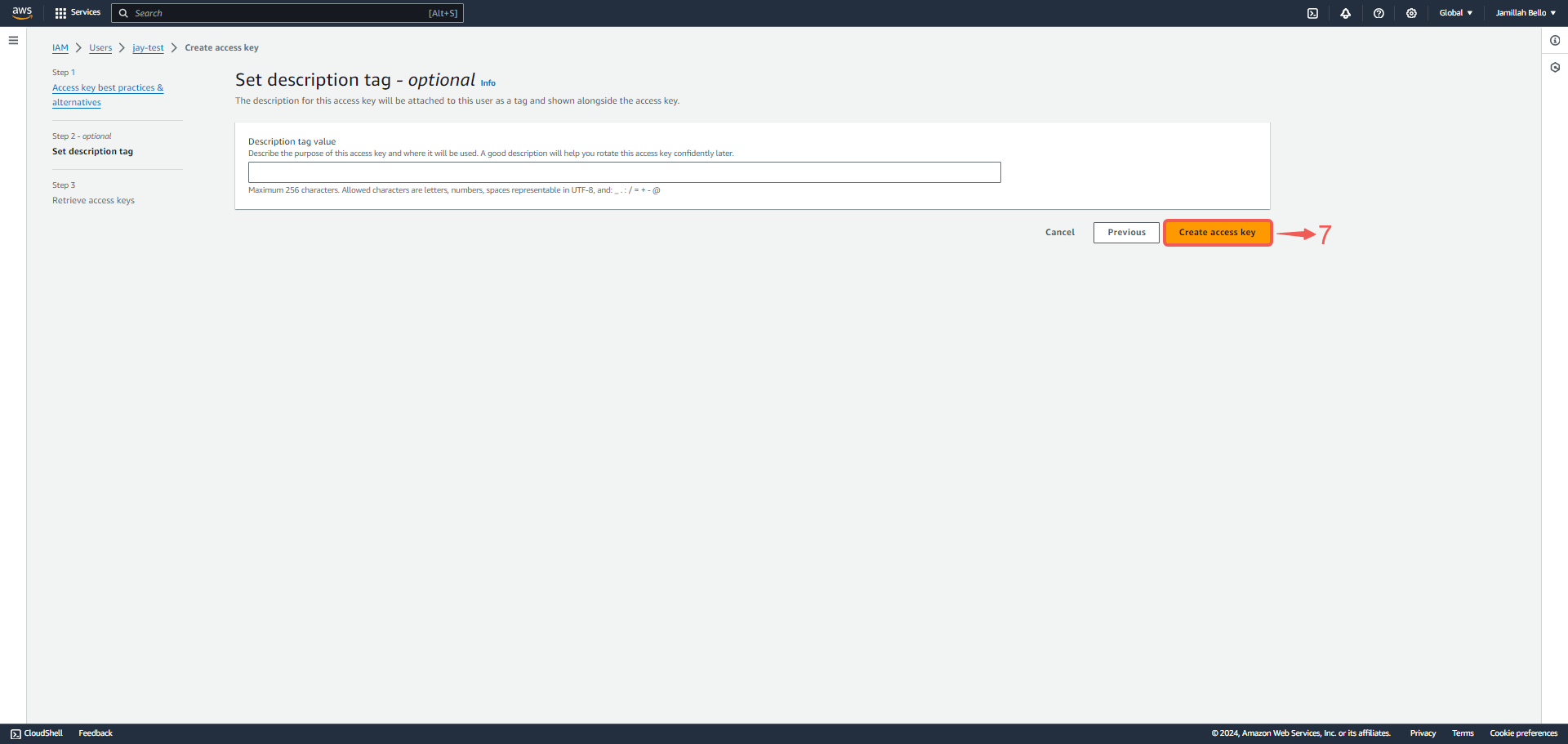
4. Click Create access key⑦.
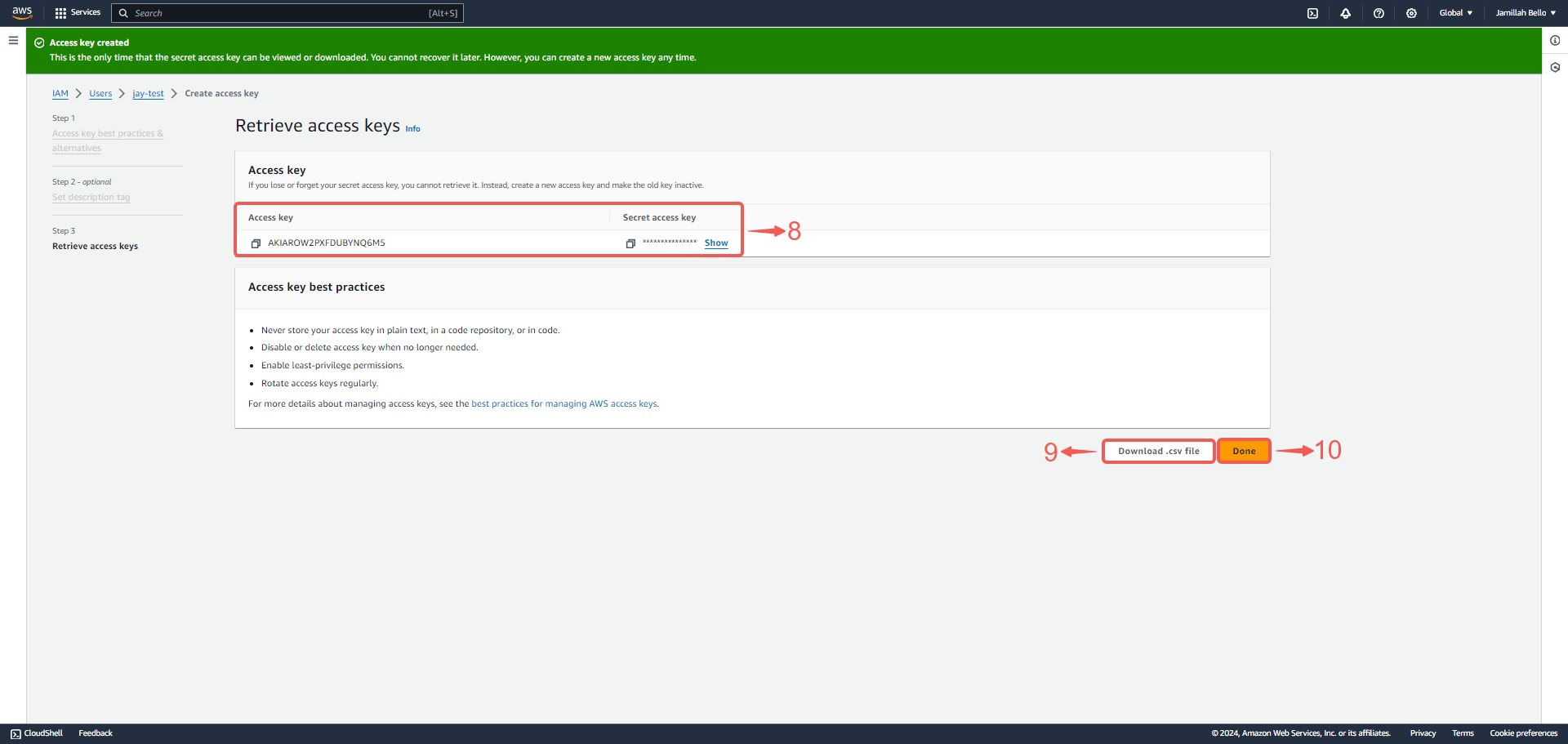
5. Your access credentials⑧ have been generated. Download them using the Download .csv file⑨ button and then click Done⑩.
Now you’re equipped to create IAM users with programmatic access, allowing your developers and DevOps engineers to automate tasks and streamline your AWS workflows. Remember, the principle of least privilege is key – assign only the permissions necessary for each user. With IAM, you can achieve both security and efficiency in your AWS environment.